Cyber Conflicts and Sovereignty: A Legal Analysis within IHL and ICL Frameworks
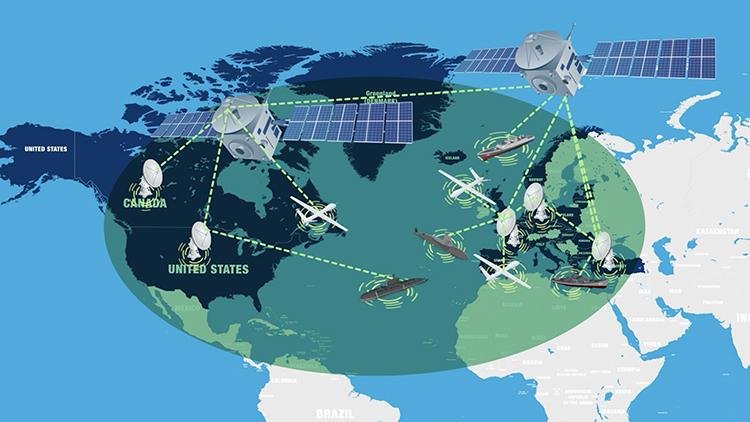
Rapid technological innovation has altered the nature of warfare, making cyberattacks a powerful weapon available to nation-states. Cyber warfare is a type of conflict that